July 14, 2020
United States
Documents released during the BlueLeaks dump shed light on US Law Enforcementās troubles with intercepting and spying on encrypted messaging apps. This concern came up multiple times during a search through the leaks, with the most commonly mentioned apps being Whatsapp, Telegram, Wickr, Signal, and Kik.
These documents also prove, that despite the pervasive and long reach arm of US law enforcement, there are still ways law abiding citizens can maintain their privacy online.

The first document, dated May 14, 2020, talks about how terrorists and criminals are switching over to encrypted messaging apps, and it is causing problems with āreal-timeā data interception a.k.a electronic surveillance. The report cites how the increasing use of encryption coupled with more restrictive privacy laws are making law enforcement snooping harder.
Law enforcement agencies face challenges when attempting to access real time [data] or data stored on cell phones or computers due to encryption, even with a warrant based on probable cause. Encryption creates difficulty in uncovering evidence of an individualās motives or criminal activities.
Source: https://drive.google.com/file/d/1oUuH-jNvlWs46H8GVjryZH3IapRvQbSQ/view?usp=sharing
Even if the police go to one of these app providers with a warrant in hand, the information they receive will either be encrypted, thus useless, or the company wonāt have message data on their servers at all. The FBI is basically asking for the tech companies to circumvent this.

The second document is from the Wisconsin Statewide Information Center. This document date September 2015, shows that encryption has been of concern for law enforcement for some time. Interestingly, this government cites the reason for people using encryption as increased awareness of government surveillance.
Increased public awareness of government surveillance has contributed to the rising consumer demand for covert messaging apps.
Source: https://drive.google.com/file/d/123hiIFU7QCDyU73gj_42zSVojqXZrtGg/view?usp=sharing
The document goes on to say forensic examiners have trouble getting into password protected or encrypted devices. It stresses the importance of getting suspects to fork over that information during interrogations. Some users upload their message-backups to a cloud, so itās possible for police to apply for a warrant and seize information through that channel.
Another interesting note, while most messaging apps alert users when law enforcement request access to their records, the police will usually seek a āgag orderā, essentially preventing them from telling the affected user.
The document cites a report by the Utah Statewide Information Center that points out it has intelligence that Militia Extremists in that state were using Wickr to mask their communications. Not only does this show the fusion centers are actively monitoring Americans, they commonly complain about how encryption makes spying more difficult.
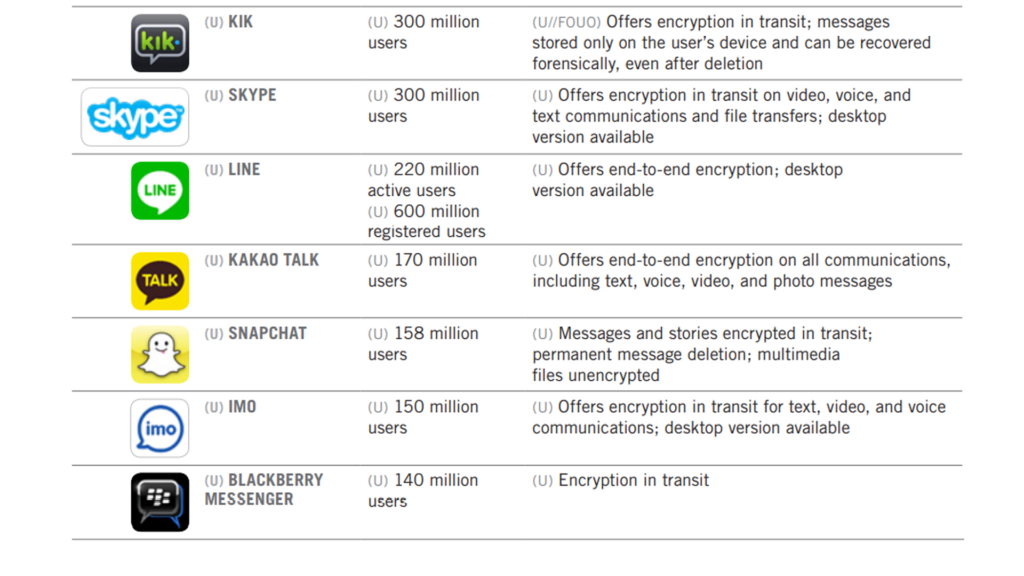
The third document, released sometime in 2017 by the National Counter Terrorism Center shows that the federal intelligence agencies kept tabs on up and coming technology and shared reports with law enforcement. It features well known apps, but also mentions lesser known apps like SureSpot and ChatSecure.
The only detail that was not publicly, or at least commonly known, is the fact that deleted Kik messages can recovered forensically.

The forth report, released by the Arizona HIDTA Investigative Support Center shows they were worried about Mexican drug traffickers using reprogrammed Blackberry devices to avoid police surveillance. It cites how drug traffickers can turn off calling and texting, then stick to encrypted email, to try and fool law enforcement into thinking their phones are inactive.
This is not necessarily new news, but gives further perspective into how US law enforcement perceived the issue. In 2019, the CEO of Phantom Secure was busted for selling devices with these exact features to Mexican drug lords.
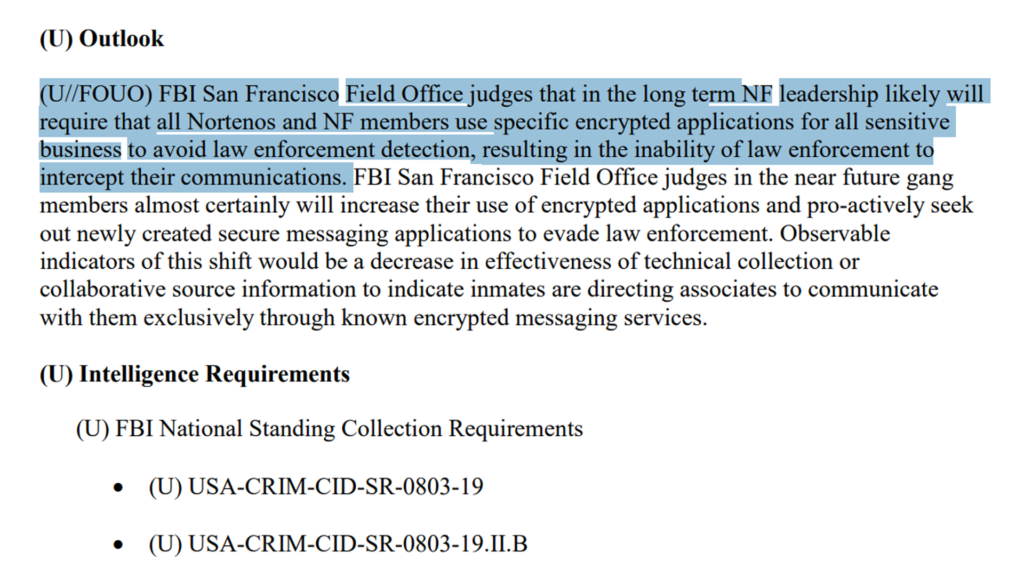
The final document, released by the FBI San Francisco in August 2019, contains exclusive information on the Nuestra Familia and Norteno Gang Membersā use of encryption, specifically within prisons. It talks about how gang members told each other the virtues of using Wickr or Signal to evade law enforcement.
These document seems to imply that law enforcement canāt get into either app, and that any communication done through either device is impenetrable.
FBI San Francisco Field Office judges that in the long term NF leadership likely will require that all Nortenos and NF members use specific encrypted applications for all sensitive business to avoid law enforcement detection, resulting in the inability of law enforcement to intercept their communications.
Source: https://drive.google.com/file/d/1WoKg1DGi_Pf5qjq63nqbBcm8nxu_Igqv/view?usp=sharing
Despite these revelations, encrypted messaging apps should not be viewed as a silver bullet. A few years back, The FBI was able to successfully gain entry into the San Bernardino shooterās iPhone. Recently, Dutch Police broke into EncroChat, an encrypted messaging app used by drug criminals in that country.
However, just because they are not silver bullets, does not mitigate the fact they are advantageous for any security minded, privacy-valuing individual. Given law enforcementās long history of spying on citizens, and finding backdoors into messaging apps, itās important to keep on top of the latest trends, and to always practice good security hygiene.
You never know where your private messages could end up, or who is listening in.
Article by: Mark Slapinski
Disclaimer: Access to these files is for educational purposes only. These files were originally made public by DDoSecrets at hunter.ddosecrets.com/datasets/102. It has since been mirrored on BlueLeaks.io, and the raw documents are being shared by many journalists and academics on Reddit and Twitter.
- FBI, Office of Private Sector
May 14 2020
Google Drive - View or Download
https://drive.google.com/file/d/1oUuH-jNvlWs46H8GVjryZH3IapRvQbSQ/view?usp=sharing
File Dropper - Download
http://www.filedropper.com/pdf1_1 - Wisconsin Statewide Information Center, Field Analysis Report
Sep 29, 2015
Google Drive - View or Download
https://drive.google.com/file/d/123hiIFU7QCDyU73gj_42zSVojqXZrtGg/view?usp=sharing
File Dropper - Download
http://www.filedropper.com/pdf2_1 - National Counter Terrorism Center, Unclassified Report
Circa 2017
Google Drive - View or Download
https://drive.google.com/file/d/1Bb_f8mS-bsoItNSwEDr8iOnyMNi6Z_LT/view?usp=sharing
File Dropper - Download
http://www.filedropper.com/pdf3 - HIDTA Investigative Report Center, Situational Awareness Report
June 5, 2017
Google Drive - View or Download
https://drive.google.com/file/d/1YsmBmUmL3KIHpM9Be8AFAJf-b_DCrB9C/view?usp=sharing
File Dropper - Download
http://www.filedropper.com/pdf4_1 - FBI San Francisco, External Intelligence Note
Aug 20 2019
Google Drive (View / Download)
https://drive.google.com/file/d/1WoKg1DGi_Pf5qjq63nqbBcm8nxu_Igqv/view?usp=sharing
File Dropper (Download)
http://www.filedropper.com/pdf5